Hart Protocol Ppt For Mac
Sep 19, 2016 If you have 4-20mA process instrumentation, you probably have HART capabilities. Let us show you how it works. HART allows the use of up to two masters: the engineering console in the control room and a second device for operation on site, e.g. A PC laptop or a handheld terminal. The most important performance features of the HART protocol include: 4proven in practice, simple design, easy to maintain and operate.
Warframe how to rank up mods fast. This alert has been successfully added and will be sent to:
You will be notified whenever a record that you have chosen has been cited.
To manage your alert preferences, click on the button below.
Manage my AlertsPlease log in to your account
Save to Binder
Create a New Binder
WirelessHART is a secure and reliable communication standard for industrial process automation. The WirelessHART specifications are well organized in all aspects except security: there are no separate specifications of security requirements or features. Rather, security mechanisms are described throughout the documentation. This hinders implementation of the standard and development of applications since it requires profound knowledge of all the core specifications on the part of the developer.
In this paper we provide a comprehensive overview of WirelessHART security: we analyze the provided security mechanisms against well known threats in the wireless medium, and propose recommendations to mitigate shortcomings. Furthermore, we elucidate the specifications of the Security Manager, its placement in the network, and interaction with the Network Manager.
- HART Communication Foundation (HCF). 9390 Research Blvd., Suit I-350 Austin TX 78759 USA. http://www.hartcomm2.org/index.html.Google Scholar
- The ISA100 Standards: Overview & Status. http://www.isa.org/source/ISA100.11a_Release1_Status.ppt.Google Scholar
- Network Management Specification, HCF_SPEC-085, Revision 1.1. HART Communication Foundation, May 2008.Google Scholar
- TDMA Data Link Layer Specification, HCF_SPEC-075, Revision 1.1. HART Communication Foundation, May 2008.Google Scholar
- Wireless Command Specification, HCF_SPEC-155, Revision 1.1. HART Communication Foundation, May 2008.Google Scholar
- WirelessHART Device Specification, HCF_SPEC-290, Revision 1.1. HART Communication Foundation, May 2008.Google Scholar
- IEC approves WirelessHART. Control Engineering, Vol. 55 Issue 10 Pages 34-34, October 2008.Google Scholar
- C. Alberts and A. Dorofee. Managing Information Security Risks: The OCTAVE Approach. Addison Wesley, 09 July 2002. Google Scholar
- A. Bogdanoy. Multiple-differential side-channel collision attacks on aes, lecture notes in computer science. 10th international workshop on Cryptographic Hardware and Embedded Systems, 5154(2):30-44, 2008. Google Scholar
- L. Buttyan and J.-P. Hubaux. Security and Cooperation in Wireless Network. Cambridge University Press, 2007. Google Scholar
- J. R. Douceur. The sybil attack. 1st International workshop on Peer-To-Peer Systems (IPTPS), March 2002. Google Scholar
- M. Dworkin. Recommendation for Block Cipher Modes of Operation: The CCM Mode for Authentication and Confidentiality. NIST Special Publication 800-38C, May 2004. Google Scholar
- Y.-C. Hu, A. Perrig, and D. B. Johnson. Wormhole attacks in wireless networks. IEEE Journal on Selected Areas in Communications, 24(2):370-380, February 2006. Google Scholar
- A. N. Kim, F. Hekland, S. Petersen, and P. Doyle. When hart goes wireless: Understanding and implementing the wirelesshart standard. IEEE International Conference on Emerging Technologies and Factory Automation, pages 899-907, September 2008.Google Scholar
- Y. W. Law, M. Palaniswami, L. V. Hoesel, J. Doumen, P. Hartel, and P. Havinga. Energy-efficient link-layer jamming attacks against wireless sensor network mac protocols. ACM Transactions on Sensor Networks (TOSN), 1(5):71-80, February 2009. Google Scholar
- T. Lennvall, S. Svensson, and F. Heklan. A comparison of wirelesshart and zigbee for industrial applications. IEEE International Workshop on Factory Communication Systems, pages 85-88, May 2008.Google Scholar
- C. Leung. Evaluation of the undetected error probability of single parity-check product codes. IEEE Transactions on Communications, 31(2):250-253, 1983.Google Scholar
- A. Liu and P. Ning. Tinyecc: A configurable library for elliptic curve cryptography in wireless sensor networks. International Conference on Information Processing in Sensor Networks, 2008. IPSN '08, pages 245-256, April 2008. Google Scholar
- R. C.-W. Phan. Impossible differential cryptanalysis of 7- round aes. Information Processing Letters, 91(1):33-38, 2004. Google Scholar
- H. K. D. Sarma and A. Kar. Security threats in wireless sensor networks. IEEE A&E Systems Magazine, June 2008.Google Scholar
- W. Simpson. PPP in HDLC Framing, RFC 1549. IETF, Network Working Group, Fremont, California 94538 USA, December 1993.Google Scholar
- J. Song, S. Han, A. K. Mok, D. Chen, M. Lucas, and M. Nixon. Wirelesshart: Applying wireless technology in real-time industrial process control. Real-Time and Embedded Technology and Applications Symposium, 2008(RTAS-08), pages 377-386, April 2008. Google Scholar
- W. Stallings. Data and Computer Communications, pages 277-282. Prentice Hall, eighth edition, 2006. Google Scholar
- H. F. Tipton and M. Krause. Information Security Management Handbook, pages 1129-1135. Auerbach Publications, sixth edition, 2007. Google Scholar
- H. Wang and Q. Li. Efficient implementation of public key cryptosystems on mote sensors. In Proceedings of International Conference on Information and Communication Security (ICICS), pages 33-38, 2004. Google Scholar
- H. Wang, B. Sheng, and Q. Li. Elliptic curve cryptography-based access control in sensor networks. International Journal of Security and Networks, 1(3/4):127- 137, 2006. Google Scholar
- D. Whiting, R. Housley, and N. Ferguson. Counter with CBC-MAC (CCM), RFC 3610. IETF, Network Working Group, Fremont, California 94538 USA, September 2003. Google Scholar
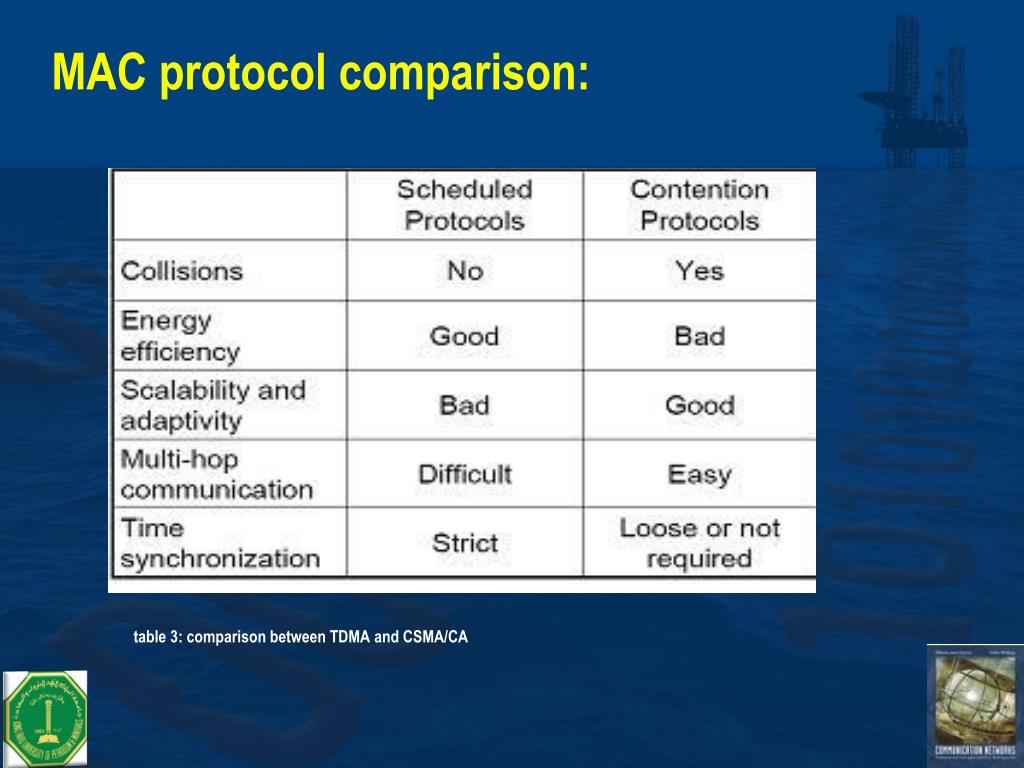
Security considerations for the wireless HART protocol
Login options
Check if you have access through your login credentials or your institution to get full access on this article.
Sign inFull Access
Published in
1765 pagesIn-Cooperation
Publisher
IEEE Press
Publication History
Qualifiers
- ARTICLE
Funding Sources
Article Metrics
- Total CitationsView Citations
- Total Downloads
- Downloads (Last 12 months)0
- Downloads (Last 6 weeks)0
Other Metrics
Digital Edition
View this article in digital edition.
View Digital EditionIt’s been weeks since Apple released its new operating systems, iOS 10 and mac OS Sierra. The new updates brought security patches, features and upgrades. Siri assistant has finally arrived on desktops, and an exciting universal clipboard allows you to select photos from an iPhone device and paste them directly on the desktop.
Snap the two hoses into the window adapter and attach the window adapter to the plexiglass part of the window installation kit. Plug in the cord and turn on the air-conditioner. Raise it up to the highest speed and move to the outside of the house to see how it is venting. How to Install a Window Air Conditioner in a Crank Window. Step 1 - Open the Window. First, open the window by using its crank handle. Continue to crank the window open until you get to the stopper point. Step 2 - Take out the Screws. Step 3 - Take out the Operator Control Arm Clip. Step 4 - Take. How to Install a Portable Air Conditioner in a Casement/Crank Window. First measure the window in order to know what size Plexiglas insert you’ll need. You can have a piece of Plexiglas cut at your local. Once you’ve got your Plexiglas, you can begin the installation process. Installing air conditioner in crank out window.
However, with these changes, Apple has decided to leave old loose ends which could affect the security of its products. One of the changes is Apple’s departure from the PPTP encryption protocol in its built-in VPN. The reason for such a step is because of a number of security vulnerabilities found in this security protocol.
Apple has publicly announced the departure from PPTP and encouraged the use of other security protocols, such as L2TP/IPsec, IKEv2/IPsec, Cisco IPsec, and SSL VPN.
https://twitter.com/itxjamie/status/776102836874649600
PPTP (Point-To-Point Tunneling protocol) – which is considered weak encryption protocol – is also perceived as the fast communication protocol that offers better speed than other protocols. It leaves many PPTP VPN users frustrated as they are hand-tied to using third-party client applications in order to use PPTP VPN connection.
Microsoft also mentioned and advised its users to use alternative protocols in a blog post:
“iOS 10 no longer supports the PPTP VPN protocol. If you have deployed any custom profiles in Intune that use the PPTP protocol, iOS 10 will remove the PPTP connections from any VPN profiles when a user upgrades their device. Intune supports alternatives to PPTP from the IT Admin console.”
Apple has always been taken the security a top priority, which could be seen by the recent question and answers session attended by the company’s CEO, Tim Cook. There, he described encryption as “one of the things that make the public safe.” He further said:
“We feel we have a responsibility to protect our customers.”
“We believe the only way to protect both your privacy and safety from a cyber attack is to encrypt. We throw all of ourselves into this and are very much standing on principle in this.”
While departing from a PPTP connection may seem a frustration for some and a cumbersome process for organizations to update their protocols, it is also a step forward to ensure the security of those who are using VPNs for Mac and iOS devices.
Understanding the said protocols
L2TP/IPsec
L2TP (Layer 2 Tunneling Protocol) is a tunneling protocol used in VPN connection. It does not have its own encryption algorithm but relies on the encryption suite of IPsec, which authenticates and encrypts each IP packet of a communication taking place. This protocol offers a balance of speed and security as compared to PPTP.
However, L2TP is not compatible with NAT, port-forwarding becomes a necessity in some cases, and if the IP of the IPsec server changes, all clients needs to be informed of the change.
IKEv2/IPsec (VPN Reconnect)
IKEv2 (Internet Key Exchange version 2) is a tunneling protocol that uses IPsec encryption protocol over UDP port 500. Jointly developed by Microsoft and Cisco, also dubbed as “VPN reconnect,” IKEv2 provides resilience to the VPN connection. When the VPN client moves from one wireless hotspot to other, it automatically disconnects all internet activities when a VPN connection is lost and re-establishes the connection upon successful connectivity.
Mobile users specifically can benefit from such a protocol. However, it is not supported on many platforms as it is fairly new to VPN services. In many cases, they just offer a “kill switch option” as a feature in their VPN client.
Cisco IPsec
Cisco IPsec is a tunneling protocol typically used in the network infrastructure of organizations to secure the communications between Cisco routers and VPN clients. Cisco IPsec applies without affecting the individual workstations, which typically occurs in IPsec. The benefits of Cisco IPsec technology over typical IPsec protocol is that it applies to all the traffic cross the perimeter of the company’s network. There is no need to change the software on the server system. It supports remote access of offsite workers.
SSL VPN
SSL (Secure Socket Layer) VPN works similar to traditional VPN. The SSL VPN technology has grown in popularity as compared to its counterpart IPsec and allows users to connect remotely to their organizations, obtaining access to the restricted network. It adds advanced encryption technology of SSL and transmits data through an encrypted tunnel to a VPN concentrator, which gives the appearance of a user as that of the local network regardless of the actual location of the user.
Choosing Between Tunneling Protocols
When choosing between L2TP, Cisco IPsec, SSL VPN, and IKEv2/IPsec VPN solutions, consider the following:
- PPTP, unlike other protocols, does not require PKI (Public Key Infrastructure). PPTP VPN provides data confidentiality (captured packets cannot be decoded without encryption key). However, PPTP VPN does not offer data integrity (data was not modified in transit) or data origin authentication (data sent by authorized user).
- L2TP supports either preshared key or computer certificates as the authentication method for IPSec encryption protocol. Computer Certificate Authentication is the recommended method, which requires the PKI to issue computer certificates at each communication step between VPN server and VPN client. L2TP offers data confidentiality, data authentication, and data integrity. Unlike other protocols, L2TP facilitates machine authentication at IPsec layer and authentication at user level at PPP layer.
- Cisco IPsec is suitable for organizations to secure network infrastructure.
- IKEv2 support is limited to systems running Windows 7 and Windows Server 2008 R2. IKEv2 supports latest IPsec encryption ciphers. It supports mobility (MOBIKE), which handles the VPN connectivity issues, and it is a good choice for users. It provides data integrity, confidentiality, and authentication.
- SSL VPN supports the latest technology of SSL as compared to its counterpart IPsec. It is widely used in OpenVPN client. OpenVPN is an open-source software application that applies VPN techniques to create secure connections. It utilizes TLS/SSL for key exchange. It is NAT- and firewall-friendly. Though it offers strong security but it slows down the speed as compared to its counterparts.
Apple has removed PPTP support for its built-in VPN, but it doesn’t limit you from installing third-party VPN client software. However, even with third-party VPN client, it is suggested not to use a PPTP VPN connection (as it has become outdated and vulnerable to cyber attacks) when other strong security protocols are available.

About the Author:Peter Buttler is a professional security expert and lecturer. He serves as a digital content editor for different security organizations. While writing he likes to emphasize on recent security trends and some other technology stuff. You can follow him on Twitter.
Editor’s Note:The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
- вторник 07 апреля
- 16